Email is a major source of phishing and malware attacks. The Locky ransomware solely contributed to a 412% increase of malware emails in March compared to February, according to CYREN’s May 2016 cyberthreat report. While I believe that awareness and training is the most universally effective counter-measure, even that is really difficult, according to this recent study. We probably need a combination of training and technological advancements. One of the latter has to do with email authenticity. Can you trust an email’s sender address? Generally no, but you can with DMARC.
To start with, an email has two sender addresses;
- The “envelope” address, used as return address in case the email cannot be delivered. It’s communicated between MTAs in the MAIL FROM SMTP command.
- The address written in the letter itself, that you see in your email app. It’s communicated as a so-called header named “From”.
Take this email for example, that our CFO Helena received a few months ago.
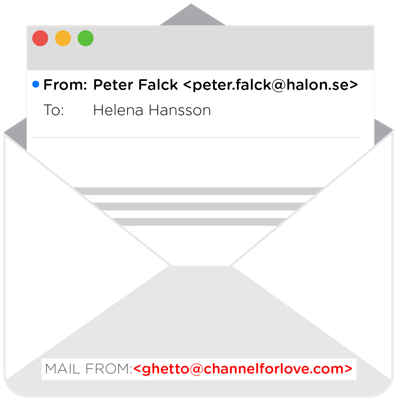
In Helena’s email app, it looks like an email coming from Peter, our CEO…
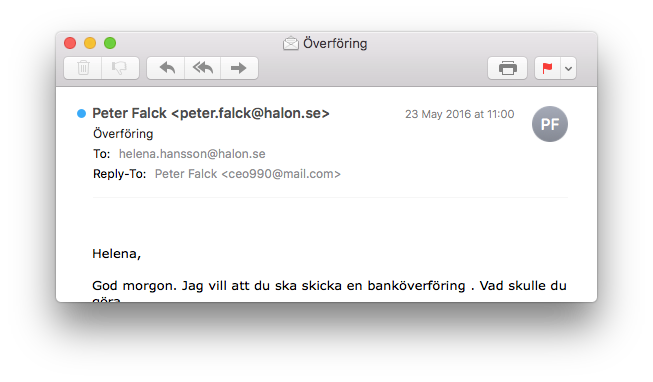
…when it in fact comes from someone else.
MAIL FROM:<ghetto@channelforlove.com> RCPT TO:<helena.hansson@halon.se> DATA Received: from p3plwbeout18-06.prod.phx3.secureserver.net (unknown [173.201.193.192]) by mail.halon.se (Halon) with ESMTPS id 05170a12-7012-11e6-bc86-0050569a261d; Mon, 23 May 2016 11:00:50 +0200 (CEST) Received: from localhost ([173.201.193.152]) by p3plwbeout18-06.prod.phx3.secureserver.net with bizsmtp id xl0p1s0013Hkz8V01l0p7m; Mon, 23 May 2016 02:00:49 -0700 X-SID: xl0p1s0013Hkz8V01 Received: (qmail 23080 invoked by uid 99); 23 May 2016 09:00:49 -0000 X-Originating-IP: 31.3.154.150 Message-Id: <20160523020047.47e0dcfe1d347a73e566ae8bed7c2532.9251012eae.wbe@email18.godaddy.com> From: "Peter Falck" <peter.falck@halon.se> Reply-To: "Peter Falck" <ceo990@mail.com> To: helena.hansson@halon.se (cut)
The envelope address, in this case “channelforlove.com”, is protected by a thing called SPF. It’s an over 10 years old and widely deployed standard that prevents spammers and phishermen from spoofing the envelope address. SPF was a major achievement for email, because it enabled receivers (email administrators, spam filters, whitelists, etc) to trust the envelope’s sender domain.
The from address, in this case “halon.se”, has not been possible to verify, until DMARC came along. Because it’s the address that the user see in the email app, DMARC is a great tool for helping prevent scamming attacks.
This particular scam is pretty easy to see through, because of the poor language and the reply-to address. Other scam emails can obviously be quite effective. A recent study by a cybersecurity company suggests that ransomware is a billion-dollar business.
DMARC is already widely deployed by senders that would otherwise see their domains abused by scammers, such as PayPal and Facebook. The fact that it’s backed by large, influential enterprises and based on the existing standards SPF and DKIM, has probably been a contributing factor to its success. The specification was published in 2012, and within a year 60% of consumer mailboxes were protected. Support in software is quite good, and Halon implements it since 2013, as it’s part of our open source DKIM library.
Halon recommends that you start using DMARC, to help protect yourself and others from getting scammed. Contact us, and we’ll help your organisation set it up.