The Safe Link technology was recently launched by Microsoft through Office 365. The goal of this technology is to rewrite all URL’s in email to a URL classification service, so at the time of user-clicks it’s possible to reclassify a URL. This method is preferred as spammers more often replace the phishing URL’s site content after a message is being scanned, hence there is a need of reclassification later. Safe link is Microsoft’s “best-effort” to do so.
“For messages in HTML, Safe links identifies any link that uses the HREF attribute. For messages in plain text, Safe Link uses custom logic to identify any text resembling a URL.”
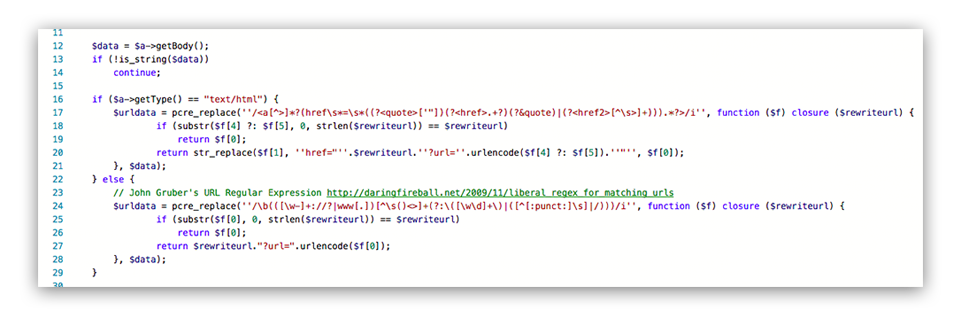
This method should work correctly in all MUA (email clients). From the web mail to your iPhone’s Mail app. However, replacing a URL in HTML as text is difficult. Just let me demonstrate how easy it is to fool Microsoft’s Safe Link:
<a x=">" href="http://badurl.com">click me</a>
^--- the regex? engine stops to detect the <a> tag here, and leaves the href unchanged.
Another obvious way to fool the Safe Link re-writer is to use a <form>-tag (it may not work in all email clients). You may be safe until spammers figure this out.
<form action="http://badurl.com"><input value="click me"></form>
If it’s this easy to fool, should it be done in another way or perhaps complemented with additional safeguards, preferably in the MUA (web mail, Outlook.app, etc)? I think so, and would have expected that Microsoft tried harder.
First suggestion; when rendering the email replace all links by asking the rendering engine what it has rendered
$("a").each(function () { /* all links are detected foolproof */ });
Second suggestion; Microsoft could surely use one of there own HTML parsers (like the one in the Edge engine) to detect where URL’s are located in the message in order to properly replace them, it’s probably better than a regex.
If customers are activating and paying for Safe Link they should be able to expect more value for their money and some more security.
In Halon you can do the same simple URL rewriting using this HSL code.